前言
近日在一台新服务器上完成了公司项目演示环境的迁移,遂记录下大致步骤
步骤
Linux云服务器操作系统:CentOS8
- 1、搭建环境(安装以下所需环境,附各命令)
(1)、.netcore-sdk1
| sudo dnf install dotnet-sdk-3.1
|
1
| sudo dnf install aspnetcore-runtime-3.1
|
1
| sudo yum install -y nginx
|
1
| sudo yum module install nodejs
|
- 2、由于发现新服务器安全组未开启80、443端口,故开启
- 3、设置全局环境变量vim /etc/profile
最后一行加入export ASPNETCORE_ENVIRONMENT=Stagingsource /etc/profile
- 4、在根目录准备好前后台所需文件夹
mkdir /root/Upsfh.AppMaster
mkdir /root/Upsfh.MgMaster
mkdir /opt/Upsfh.ManageMx.Static
- 5、配置云企业网实例
https://help.aliyun.com/document_detail/65901.html?spm=a2c4g.11186623.6.559.5e4c2de0zLi3C0
(1)、在账号A配置云企业网实例
(2)、此时需要到账号B进行云企业网跨账号授权配置成功后,将22端口开放给CICD服务器的内网地址,即能进行内网之间的跨账号访问
- 6、修改.gitlab-ci.yml文件,在gitlab设置 -> CICD中设置相应变量
- 7、把服务器内网IP加到redis和rds的白名单中8、nginx配置代理
1
| vim /etc/nginx/nginx.conf
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
gzip on;
server {
listen *:80;
add_header Strict-Transport-Security max-age=15768000;
return 301 https://$host$request_uri;
}
include /etc/nginx/conf.d/*.conf;
}
|
1
| vim /etc/nginx/conf.d/staging-api.conf
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| server {
listen *:443 ssl http2;
server_name 域名;
ssl_certificate "证书.pem";
ssl_certificate_key "证书.key";
ssl_session_timeout 5m;
client_header_buffer_size 16k;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ecdh_curve secp384r1;
ssl_session_cacheshared:SSL:10m;
ssl_session_tickets off;
ssl_stapling on;
#ensure your cert is capable
ssl_stapling_verify on;
#ensure your cert is capable add_header Strict-Transport-Security "max-age=63072000; includeSubdomains;preload";
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
location / {
proxy_pass http://localhost:5080;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $http_host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}
|
1
| vim /etc/nginx/conf.d/staging-mx.conf
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name 域名;
ssl_certificate "证书.pem";
ssl_certificate_key "证书.key";
ssl_session_timeout 5m;
client_header_buffer_size 16k;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ecdh_curve secp384r1;
ssl_session_cache shared:SSL:10m;
ssl_session_tickets off;
ssl_stapling on;
#ensure your cert is capable ssl_stapling_verify on;
#ensure your cert is capable add_header Strict-Transport-Security "max-age=63072000; includeSubdomains; preload";
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
location / {
add_header Cache-Control 'no-cache, must-revalidate, proxy-revalidate, max-age=0';
root /opt/Upsfh.ManageMx.Static;
index index.html index.htm;
try_files $uri $uri/ /index.html;
}
location /logs {
alias /root/Upsfh.MgMaster/logs;
index index.html index.htm;
}
location /api {
proxy_pass http://localhost:5090/api;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection keep-alive;
proxy_set_header Host $http_host;
proxy_cache_bypass $http_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}
|
- 8、重启nginx
- 9、提交代码,CICD跑起来
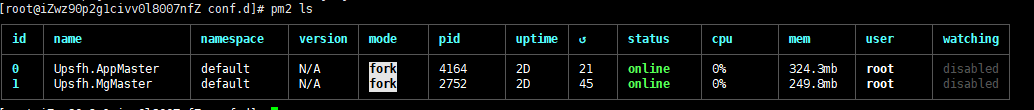
首次需要手动利用pm2启动前后台项目的守护服务1
2
| pm2 start "dotnet Upsfh.AppMaster.dll" --name Upsfh.AppMaster --env={"ASPNETCORE_ENVIRONMENT":"Staging"}
pm2 start "dotnet Upsfh.MgMaster.dll" --name Upsfh.MgMaster --env={"ASPNETCORE_ENVIRONMENT":"Staging"}
|
- 10、成功